Maximize EDR Capabilities with Email Telemetry Data
- Admin
- Oct 31, 2023
- 2 min read
Endpoint detection and response (EDR) is the key technology that now helps overburdened SOC teams staying ahead of attackers. Yet focusing on endpoint telemetry only can often prove limiting: attackers will try to breach organizations by probing the entire attack surface, not only the endpoints: from network devices exposed on the internet (i.e. exploiting zero-day vulnerabilities) to employee email accounts susceptible to phishing techniques and account takeover.
For the latter use case, email telemetry can enrich the SOC data lake and provide better context and actionable intelligence. EDR/XDR vendors already having email protection solutions in their portfolio are particularly well positioned to just that.
Trend Micro's XDR solution called Vision One is developing in that direction, as revealed in a recent roadmap disclosure (see here). The solution already features integration with its MS365 and Gmail protection product called Cloud App Security (CAS), and is now announcing visibility into telemetry from other email security products such as Trend Micro Email Security or TMES (the cloud prefilter solution based on MX front-ending), and even on-prem based legacy solutions such as ScanMail for Exchange, Deep Discovery Email Inspector and IMSVA.

In particular, the CAS solution consumes Microsoft's and Google APIs to provide monitoring and protection for the email flow, so it can surface the telemetry data within Vision One and provide useful contextual info for the SOC analyst, but also enable actionable response such as quarantine or delete specific messages (effectively extending from endpoint to email threat detection and response).
Below are some examples of what XDR email integration can provide.
Actionable response on specific emails in inboxes
Directly from the XDR console delete or quarantine suspicious messages found to be part of an attack chain:

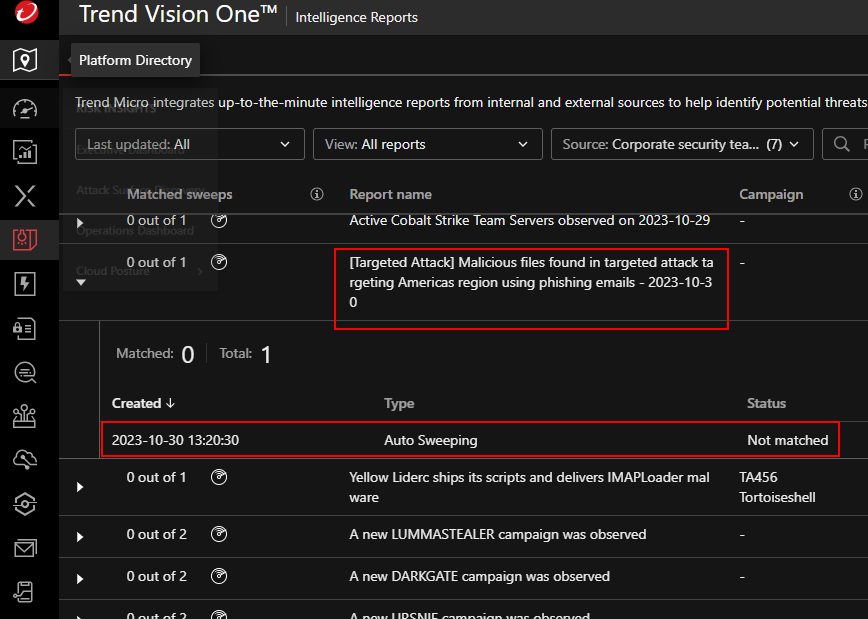
Sweeping email inboxes for IOCs
If a particular indicator of compromise is associated with a phishing campaign, automatic mailbox sweeping can find and remove such emails:
Threat hunting and search within email metadata
Search based not only on endpoint telemetry, but also on email metadata such as subject, attachment name, url links, recipients, senders (envelope and mime), email source IP addresses, etc.:

Risk management: check for misconfigurations or poor configurations
By integrating with the email protection product, Vision One can check if recipients are not covered with a best practice email filtering policy (such as phishing detection or attachment filtering):

Assess phishing risks
Based on the same recipient inventory discovered by the email product, Vision One can send phishing simulation emails and report on vulnerable users:



