Integration Cases for NDR and EDR
- Admin
- Mar 11
- 2 min read
Network Detection and Response (NDR) tends to be often overlooked in today's security stacks, which are usually heavily dependent on endpoint antimalware or Endpoint Detection and Response (EDR).
Yet, there is a case to be made for a better integration between the two security layers to enhance visibility, accelerate incident response, and reduce manual efforts.
Fortunately, APIs are maturing and most security vendors in the EDR and SIEM space now offer APIs for both data sharing (for ex. uploading indicators of compromise - IoC) and automated orchestration (for ex. quarantine an endpoint).
This opens the way to several integration scenarios.
Automated Threat Intelligence Sharing
When an EDR detects a suspicious process or malware on an endpoint, it can trigger a webhook and share threat intelligence (e.g., IP addresses, hashes, domain names) with the NDR solution.
A proper NDR must be able to quickly correlate network activity to check if other device communication is associated with the same IoCs or the same threat actor. This enriched context or alert can then be fed back into the EDR or SIEM stack.
Endpoint Isolation Triggered by Network Threat Detection
If the NDR sees potential lateral movement attempt or data exfiltration, it can send an API request to an EDR solution to isolate the affected endpoints. Conversely, it can enrich these network related alerts with endpoint and log data to gain deeper insight and determine a block verdict with much higher confidence.
Cross-Correlation for Incident Investigation
Investigators need to correlate endpoint telemetry (process execution, registry changes, etc.) with network telemetry (DNS requests, traffic flows and the like). For ex. a security analyst queries the NDR API (usually from the preferred single pane of glass investigation solution) for all network traffic related to a compromised endpoint detected by the EDR. The response includes details about external connections, potential C2 domains, and affected subnets.
The analyst uses this data to pivot investigations and find related compromised assets.
Here, it's important to have the ability to look back at network traffic much before and also after an incident to uncover hidden attack paths and residual threat actor activity.
Automated Playbook Execution (SOAR Integration)
Security teams use SOAR tools (e.g., Splunk Phantom, Palo Alto XSOAR) to automate responses when both EDR and NDR detect suspicious activity. For ex. when a suspicious PowerShell script is detected on an endpoint, the SOAR solution fetches related network logs from the NDR API. If both sources confirm malicious activity, SOAR executes a playbook which blocks the related IPs in the firewall, quarantines the endpoint and notifies security teams.
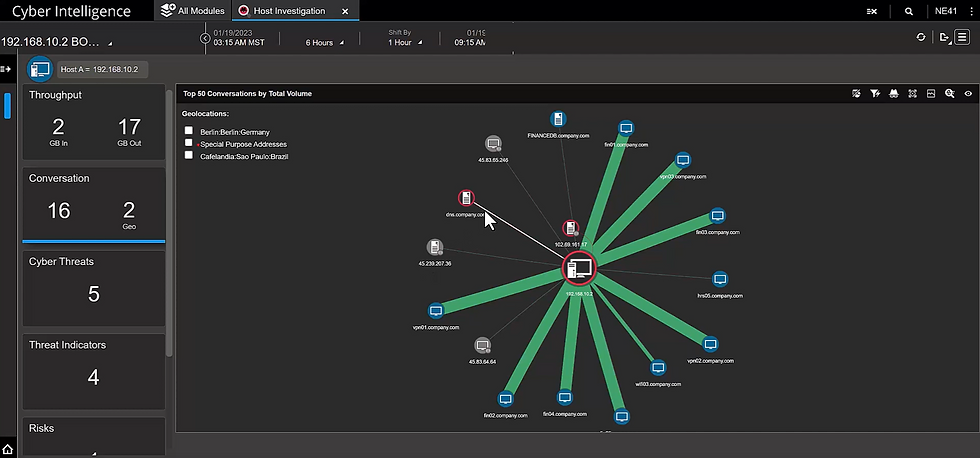
Properly architected NDR solutions can dramatically increase the efficiency and effectiveness of security teams. To find out more, join us on the upcoming webinar featuring Netscout's Omnis Cyber Intelligence (OCI) platform and explore how to move beyond NDR with a comprehensive security solution that delivers forensic and remediation tools, significantly reducing mean time to resolution.


